Raising the bar on security in embedded designs
Devices are becoming smarter and more connected, which is cause for more security concerns. Today, companies are facing design challenges to ensure strong security levels in their IoT devices and safeguard device integrity.
Governments and regulatory instances are raising awareness about the importance of IoT device security and have set high standards to streamline the approach.
- Embedded developers are faced with new challenges:
- The need to comply with different regulations within several new certification schemes
- Increasing scalability requirements
- The multiple MCU development frameworks and real-time operating systems used in the devices today, which increase complexity levels when it comes to security
- The lack of security expertise and the need to increase their skills, which requires time and money
Stronger, more scalable security for your embedded systems
STM32Trust simplifies your approach to security. STM32 MCUs and MPUs put security at the center of the equation between developers and market regulations.
The security implementations are developed by ST in the context of security assurance and in compliance with the security schemes. They also aim to match the different requirements of the industry standards on different levels to provide more scalability.
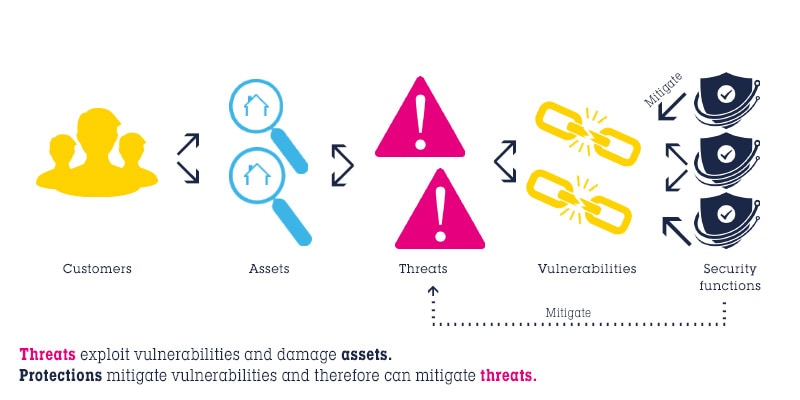
The STM32Trust solution provides developers with a robust, multilevel strategy to enhance security in their new product designs. It is based on our STM32 microcontrollers and microprocessors, combined with our STSAFE secure elements.
With a set of 12 security functions offering hardware, software, and design services from ST and third parties, STM32Trust complies with the new requirements of national regulations and security standards for applications.
Fast track your design journey with certified security
- STM32Trust relies on several security certification schemes to increase your level of confidence in the security implementations, including:
- Platform Security Assurance (PSA) defined by Arm®
- Security Evaluation Standard for IoT Platforms (SESIP) defined by Global Platform
The STSAFE secure elements supported by STM32Trust are Common Criteria EAL5+ certified.
This assurance level allows designers to use our security framework with more confidence and meet the application requirements of their security standards, such as PCI, UL-2900, IEC 62443, ETSI EN 303 645, FIPS-140-2, IoXT and many others.

