Secure Boot and Secure Firmware Update (SBSFU)
Secure Boot ensures the integrity and authenticity of the application firmware that runs inside a device.
Secure Firmware Update allows you to authenticate and verify the integrity of the required field updates.
- two implementation schemes
- X-CUBE-SBSFU, implementing the SBSFU mechanisms: easily set up all STM32 memory-protection mechanisms to isolate Secure Boot and Firmware Update functions from the main application. A reference implementation of ST's secure element, STSAFE, which maximizes the security level of the final application, is included. STM32L4 implementation also offers secure storage.
- TFM_SBSFU, implementing the same mechanisms on devices loaded with TF-M (Trusted Firmware-M), and delivered with STM32Cube packages.
| Part Number | Status | Type |
| X-CUBE-SBSFU | Active | Embedded Software |
| STM32CubeL5 | Active | Embedded Software |
| STM32CubeU5 | Active | Embedded Software |
| STM32CubeH5 | Active | Embedded Software |
Secure Firmware Installation (SFI)
The Secure Firmware Installation solution, available on STM32L4, STM32H5, STM32H7, STM32L5, STM32U5, STM32WBA, and STM32WL microcontrollers, provides protection when devices are being programmed for the first time. The solution will be extended to additional STM32 platforms.
This solution offers a complete toolset with the Trusted Package Creator software package to encrypt OEM binaries, the STM32CubeProgrammer to securely flash the STM32, and the STM32HSM to transfer OEM credentials to the programming partner.
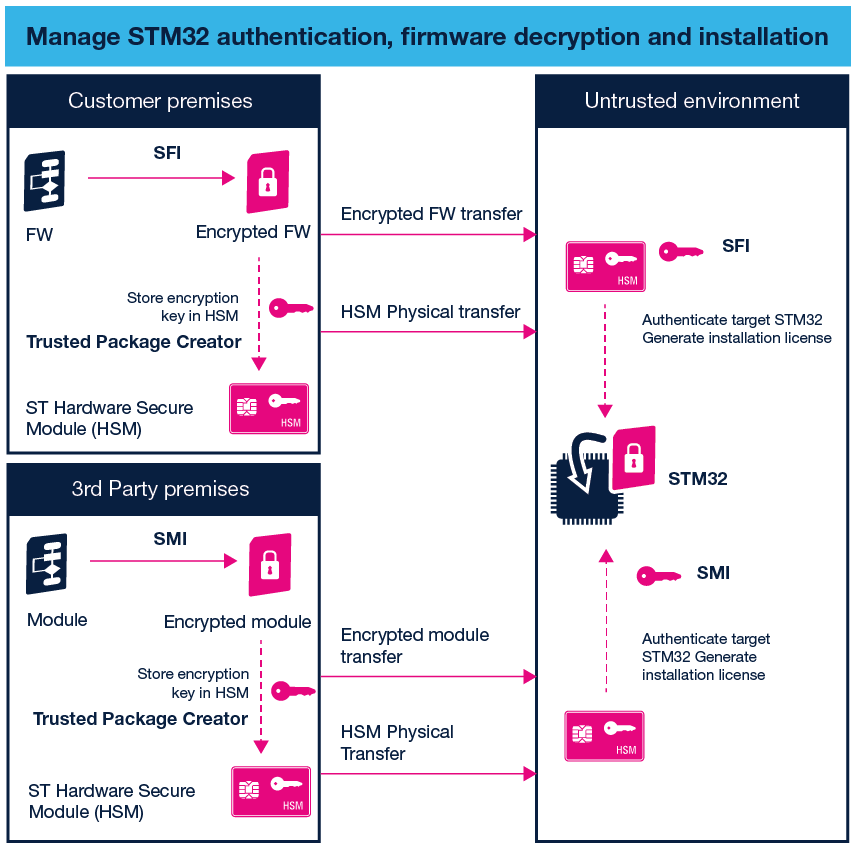
After firmware development and validation, designers can securely encrypt binary files using the Trusted Package Creator software, and store their credentials into a dedicated smartcard, such as the hardware security module STM32HSM. The STM32CubeProgrammer or SFI recommended partner programming tools can then be implemented to securely program STM32 MCUs in untrusted environments, such as EMS manufacturing lines.
STM32CubeProgrammer
The STM32CubeProgrammer includes the STM32TrustedPackage Creator tool which allows the generation of SFI and SMI encrypted images for STM32 devices embedding SFI. The tool is available in both CLI and GUI modes for free.
The SFI format is an encryption format for firmware created by ST. It uses AES algorithm to transform a firmware solution in Elf, Hex, Bin or Srec formats into an encrypted and authenticated firmware in SFI format. An SFI firmware image is composed of a header and several areas. The areas are usually contiguous firmware areas. The last area is the configuration area containing the option byte values to be programmed when the SFI is complete.
| Part number | Description |
| STM32CubeProg | STM32CubeProgrammer software for programming STM32 products |
STM32HSM
The STM32 Hardware Security Module is used to secure the programming of STM32 products to avoid product counterfeiting during the manufacturing process.
| Part Number | Status | Type |
| STM32HSM-V2 | Active | Development Tools |
Cryptographic solutions
ST offers several cryptographic solutions. They can be based on hardware implementations, with or without side-channel protection. Several sets of libraries are also available to meet the requirements of practical use cases:
Cryptographic libraries
- X-CUBE-CRYPTOLIB: this ECCN 5D002-classified software solution is based on the architecture of the STM32Cube package and includes a set of crypto algorithms based on firmware implementation. Ready to use in all STM32 microcontrollers and certified NIST CAVP
- TF-M Crypto: cryptographic service, as delivered within TF-M reference code
- OP-TEE Crypto: cryptographic service, as delivered within OP-TEE reference code
- Side channel resistant Crypto Lib: ST offers a SCA-resistant implementation of cryptographic algorithms. Available on-demand on some specific part numbers. Please contact your nearest sales office.
| Part Number | Status | Type |
| X-CUBE-CRYPTOLIB | Active | Embedded Software |
| STM32CubeL5 | Active | Embedded Software |
| STM32CubeU5 | Active | Embedded Software |
Trusted Execution Environment software solutions
Secure Manager
- STM32Trust TEE
- Simplify developer’s security journey
- Seamlessly connect to clouds and servers
- Provide multi-tenant IP protection
The Secure Manager is a turnkey solution to implement the Platform Security Architecture (PSA) for Cortex-M faster. It is a system-on-chip solution delivered in binary form only and sublicensed to our developers. It is maintained and certified by ST and is built for long time support (LTS).
- uRoT: the updatable Root of Trust that includes Secure Boot and Secure Updates.
- Secure Manager core: a secure partition manager implementing up to level 3 isolation of modules and services.
-
- Cryptography
- Secure and Trusted Storage
- Attestation
Architectural view:
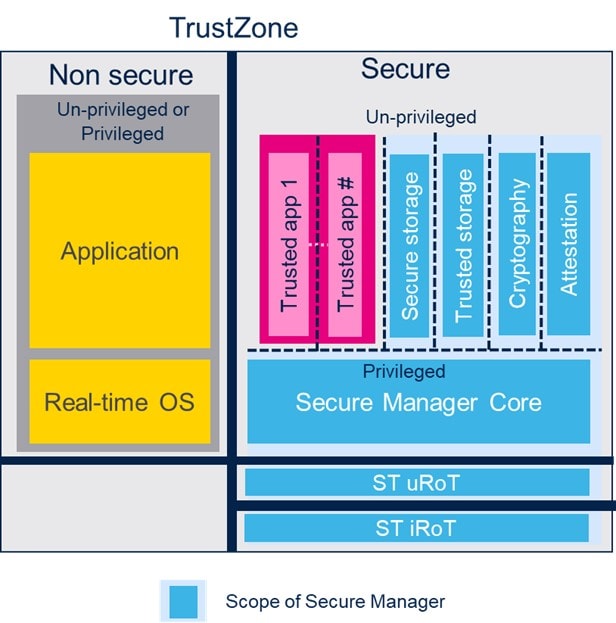
The Secure Manager allows users to either concentrate on the application development and use the arm PSA API services or add Trusted apps or Modules within the TEE trusted area. It is compatible with Trusted Firmware-M (TFM) in API and functionality.
For API versioning and detailed functionalities, please refer to the documentation available on ST’s Secure Manager webpage.
The STM32 community gets access to various Trusted applications from ST or third parties. ST continuously updates and renews these applications.
| Trusted app | Supplier | Product | |
| keySTREAM late provisioning | Kudelski | The KTA (keySTREAM Trusted Agent) is a trusted library used to manage a Root of Trust within a Secure Manager. It connects to the Kudelski IoT keySTREAM Platform, which securely provisions millions of devices using PKIaaS. The Kudelski IoT keySTREAM security management system automates the entire process, allowing for zero-touch provisioning at scale. This system offers full IoT lifecycle management capabilities, including transferring ownership, creating/deleting credentials, revoking devices, and managing their disposal/refurbishment. | STM32H5 |
-
- Dedicated to developers willing to concentrate on the application development and use the Secure Manager services.
- Provided with non-secure application examples.
- Freely available for download under a clickthrough production license
-
- Dedicated to secure modules (Trusted apps) development.
- Provided with complete examples
- Available for download under a specific and development license only
Check out ST’s Secure Manager webpage for further details and product compatibility.
Trusted Firmware-M (TFM)
The Trusted Firmware-M software implementation is a reference implementation of the Platform Security Architecture (PSA) for Cortex-M ARMv7-M and Armv8-M.
- secure firmware with support for PSA Level 1 and 2 isolation on Armv8-M
- interfaces exposed by secure firmware to a non-secure side
- a secure firmware model with non-secure application examples
-
- secure storage
- attestation
- cryptography
| Part Number | Status | Type |
| STM32CubeL5 | Active | Embedded Software |
| STM32CubeU5 | Active | Embedded Software |
| STM32CubeH5 | Active | Embedded Software |
| STM32CubeWBA | Active | Embedded Software |
Trusted Firmware-A
Usually shortened to TF-A, Trusted Firmware-A is a reference implementation of the secure-world software solution provided by Arm. It was first designed for Armv8-A platforms and has been adapted by ST for Armv7-A platforms. Arm is transferring the Trusted Firmware project to be managed as an open-source project by Linaro.
TF-A is used as the first-stage boot loader (FSBL) on STM32 MPU platforms when using the trusted boot chain.
The code is open source, under a BSD-3-Clause license, and can be found on GitHub, along with a dedicated documentation on Trusted Firmware-A implementation.
- The power state coordination interface (PSCI)
- Trusted board boot requirements (TBBR)
- Secure monitor call convention (SMC)
- System control and management interface
Open Portable Trusted Execution Environment (OPTEE)
OPTEE is a Trusted Execution Environment (TEE), a software solution designed as a companion for a non-secure Linux kernel running on microprocessors with Arm Cortex-A cores using TrustZone technology. OPTEE APIs are defined by the GlobalPlatform API specifications to which they belong.
- Isolation: the TEE provides isolation from the non-secure OS and protects the loaded Trusted Applications (TAs) from each other using underlying hardware support
- Small footprint: the TEE should remain small enough to reside in a reasonable amount of on-chip memory as found on Arm-based systems
- Portability: the TEE is compatible with different architectures and available hardware, and supports various set-ups such as multiple client operating services and TEEs
- OP-TEE is delivered as part of OpenSTLinux distribution packages, available for STM32 microprocessors.
| Part Number | Status | Type |
| STM32MP1Dev | Active | Embedded Software |
| STM32MP1Distrib | Active | Embedded Software |
| STM32MP13x | Active | Microprocessors |

